Improve Document Security in the Face of ICD-10: A HIPAA Checklist
Although Health and Human Services has delayed compliance with the International Classification…
Medical Identity Theft: The Low-Hanging Fruit for Thieves
The Ponemon Institute and Medical Identity Fraud Alliance has released their 2013 Survey…
HIPAA Not an Excuse for Lack of Innovation in Hospitals and Clinics
As a 20-year practicing physician and a former hospital CIO/CMIO, I am…
Square Peg in a Round Hole: Data Privacy and Security Laws and Standards Meet Medicine 2.0
This presentation addresses in brief questions about the US health care data…
Solutions for the Top 5 Security Vulnerabilities
A recent article from HealthCareITNews.com details the top five security vulnerabilities that…
13 Tips for Fighting Mobile Device Threats in Healthcare
I've been on a bit of a roll lately with data security…
mHealth: Mitigating Mobile Security Risks
With the use of mobile devices in the healthcare industry come several…
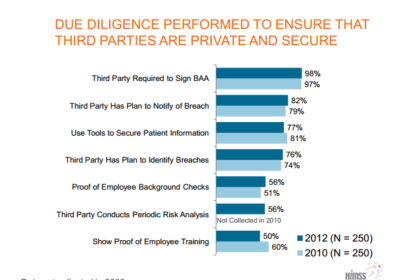
Due Diligence with Business Associates
The latest 2012 HIMSS Analytics Report: Security of Patient Data released in…
PCI Compliance with Service Providers
The PCI sub-requirements and testing procedures 12.8-12.84 concern the relationship between merchants and…