The focus seems to be on electronic records HIPAA violations; however the truth is paper violations happen more frequently. According to the HHS for the period of May 17 to June 17 there were a total of 45 breaches that involved paper; this is a stark contrast 3 breaches using Electronic Medical Records, 5 utilizing Email and 15 Network Server/Hacking incidents.
The focus seems to be on electronic records HIPAA violations; however the truth is paper violations happen more frequently. According to the HHS for the period of May 17 to June 17 there were a total of 45 breaches that involved paper; this is a stark contrast 3 breaches using Electronic Medical Records, 5 utilizing Email and 15 Network Server/Hacking incidents.
To date, 2012 saw 435 cases of HIPAA violations and affecting 20,066,249 patients. The impact of a HIPAA violation is far reaching, and not only includes a direct fiscal impact through penalty but also impacts patient perception of the infringing organization.
The HITECH Act imposes deadlines on informing the HHS Office for Civil Rights (OCR). OCR receives almost 900 complaints a month from patients. Though of the complaints received not all fall under the jurisdiction of the OCR and are redirected to the correct agency.
OCR has referred 502 cases to the Justice Department for possible criminal prosecution. Two such cases were referred in May 2012. This has lead the Justice Department to show interest in using HIPAA as a criminal enforcement tool as the FBI, federal prosecutors and other law enforcement agencies become more familiar with the law.
The privacy areas investigated most often were:
- Impermissible uses and disclosures of protected health information (PHI);
- Lack of safeguards of PHI;
- Lack of patient access to their PHI;
- Uses or disclosures of more than the Minimum Necessary PHI; and
- Lack of administrative safeguards of electronic PHI.
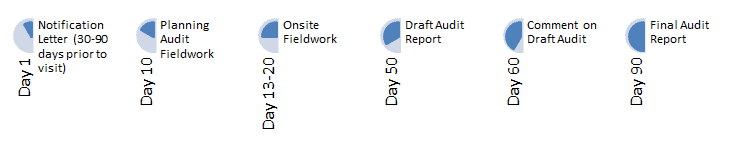
Protecting PHI should be imperative for every medical organization. To protect patients the government begun its HIPAA Audit Program in November 2011. The audit is designed to be completed within 90 days from the first day of the site visit.
HIPAA Audit Timeline:
Today’s medical field has more ways to access PHI than ever before. To protect patients as well as the organization, providers should implement strategies that protect PHI. That may include moving from a paper system to an EMR, removing paper from the patient care process, or enhancing your current network security standards.
So how can you protect yourself?
Check out an article that we wrote’ “Are you at risk to be on the “Wall of Shame” for breaches in patient privacy?” to learn more.
What are your thoughts?
Have an idea how to improve our healthcare system? Share your ideas below.