Due to the overwhelmingly positive response to an earlier blog post entitled “Paper Records More Susceptible to Breach than Any Other Medium – are you next?”, I decided to dig deeper into the data provided by the U.S. Department of Health & Human Services.
The organization provides a data of breaches affecting 500 or more individuals. While a breach that impacts 1 patient is important to rectify, the department chose 500 to be of material consequence. There were 435 breaches recorded and observed by the HHS Office for Civil Rights.
Avoidable HIPAA Breaches
It is interesting to note that the breaches that occur are avoidable. The table below examines that type of breaches that occurred in the dataset. While there are different mediums containing Patient Health Information (PHI), when stored locally either physically or digitally they are vulnerable to intruders.
| Breach Type | Breach Count |
| Theft | 238 |
| Unauthorized Access | 93 |
| Improper Disposal | 75 |
| Hacking Incident | 26 |
| Loss | 3 |
How to Protect PHI (Patient Health Information)
When examining breach types it is important to identify differences and how to protect PHI. Theft can occur physically or digitally. It is difficult to protect physical records and require secure location and incur storage costs. Storing physical patient files does not capture a history of access.
This leads to Unauthorized Access, including employee access or mishandling of PHI. Using a digital repository for PHI allows organization administrators to identify any misuse of patient data and curb potential HIPAA breaches before they become material IF proper protocols are put in place.
Proper Software Permissions
Some Electronic Medical Record (EMR) applications and services such as referralMD allow for proper administration of PHI and employee access. All IT equipment has an end of useful life and requires proper disposal. Once this occurs the equipment can be salvaged (sold to a third party) to recover some IT investment costs.
There is nothing wrong with the practice if sensitive data is removed (with a Department of Defense wipe) or data storing hardware such as hard drives, CD/DVD’s and tape backups are destroyed. Hacking can occur both internally and externally over network resources.
Small to Medium Practices Do Not Have Required IT Skills
Organization networks can be protected with firewalls from external intruders; however PHI is still vulnerable to internal malice. Most medium and small medical organizations do not deploy proper staff to monitor network traffic continuously. Cloud services can provide a layer of protection that have the staff to monitor network traffic and enforce network security on a wide scale.
Of the 435 breaches, 116 were paper based breaches, 109 involved stolen laptops, 62 Desktop computers, 40 Networks, 70 portable devices (including portable hard drives, CD/DVD’s and tape backups). Download the full report of breaches here. Almost 15 million patients were affected by breaches by the top 10 entities with the most breaches. Unfortunately most of the incidents were avoidable and due to stolen or lost physical media
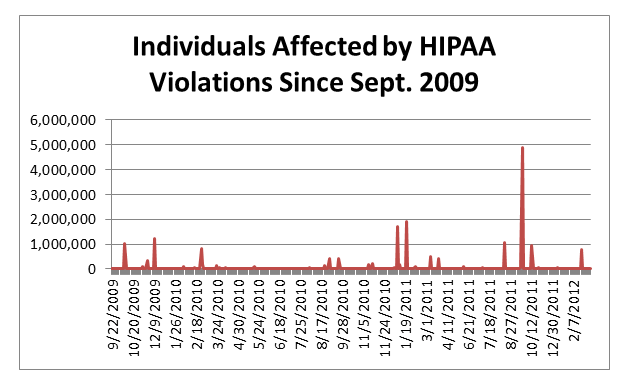
The graph below depicts the number of patients affected by HIPAA violations:
The graph below depicts the number of breaches reported per month since September 2009.
While the graph that depicts the number of breaches shows downward slope, this is misleading. Breaches that have occurred in recent months may not have been identified and/or have not been reported. OCR complaints may be filed 180 days from the date of the act or occurrence(s).
Organizations can protect themselves by adhering to HIPAA regulations and use tools such as referralMD to remain in compliance or to minimize the impact of a violation. Data from the HHS has been included in this blog post.
How do you protect your organization?
Share your thoughts below about what you do to protect your patients.