 The U.S. Department of Health & Human Services (HHS) Office for Civil Rights (OCR) announced the beginning of the 2016 Phase Two Health Insurance Portability and Accountability Act (HIPAA) Audit Program. This program is designed to evaluate the compliance efforts of covered entities and their business associates (BA) with the HIPAA Privacy, Security and Breach Notification Rules (HPSBNR).
The U.S. Department of Health & Human Services (HHS) Office for Civil Rights (OCR) announced the beginning of the 2016 Phase Two Health Insurance Portability and Accountability Act (HIPAA) Audit Program. This program is designed to evaluate the compliance efforts of covered entities and their business associates (BA) with the HIPAA Privacy, Security and Breach Notification Rules (HPSBNR).
Phase Two audits will act as an additional regulatory compliance evaluation tool that supports OCR’s current enforcement strategies. The goal of the Phase Two HIPAA audits is to ascertain best practices and proactively find and mitigate risks and vulnerabilities to protected health information (PHI). These audits will mainly be desk audits and some will be on-site evaluations.
Why are Phase Two HIPAA Audits so Important?
HIPAA security has become a lightning rod issue in the United States (U.S.) because of the growing threat of cyber-crimes that include computer hacking and identity theft. From October of 2009 through March 2016 the Secretary of HHS’s Breach of Unsecured Protected Health Information Portal documented over 157 million individuals who were affected by PHI breaches. Section 13402(e)(4) of the Health Information Technology for Economic and Clinical Health (HITECH), requires the Secretary to post a list and description of breaches of unsecured PHI affecting 500 or more individuals. Initiating Phase Two audits are a proactive measure led by the OCR to evaluate readiness, compliance and develop a strategy to reduce PHI breaches.
According to a Redspin, in their 2015 Healthcare Breach Report of PHI, the sixth annual analysis of the causes of PHI breaches reported to the OCR, Redspin found that PHI breaches have evolved from typical employee error that includes loss or theft of unencrypted portable computing devices to more sophisticated malicious acts.
“2015 was a watershed (or perhaps a ‘washout’) year in healthcare IT security,” notes the report. “In previous reports, we warned that ‘the threat from malicious outsiders—hackers—has the potential to wreak havoc on the healthcare industry.’ In 2015, havoc was wrought.”
Nine out of 10 breach incidents were the result of criminal hacking. Those occurrences amounted to 98 percent of all patient records breached in 2015. Daniel W. Berger, President of Redspin, said, “Healthcare organizations are under attack. For those entrusted to protect patient data, the security challenges are now much more difficult.”
The report also indicated that 88 percent of all records breached stemmed from the top three cases in 2015. Anthem led the pack as the largest healthcare breach in U.S. history, involving 79 million patient medical records.
The statistics on healthcare data breaches continues to be a growing concern. According to the Identity Theft Resource Center, healthcare data breaches accounted for 35.5 percent of all breaches in 2015 which surprisingly was a drop of 8.6 percent from a record high of 44.1 percent in 2014.
However, the healthcare industry is in no position to celebrate. While financial data has the greatest number of data breaches, a single PHI record is worth roughly 50 times more than a credit card or Social Security number. Medical records have detailed demographics and other sensitive information, including commercial and government insurance and prescription data. Unlike credit card numbers or other financial information, when a theft of PHI happens, the data is irrecoverable.
One in 10 Americans have been affected by large health data breaches, and employee negligence is considered the greatest security risk reported in the 2015 Ponemon Institute’s Fifth Annual Benchmark Study (PIABS) on Patient Privacy and Data Security report. Data breaches in healthcare put patient data at risk and are costly. Based on the results of the PIABS study, the survey found:
- The cost to the industry is over $6 billion annually;
- Over 40 percent of the respondents had more than five data breaches over the past two years;
- The average cost of a data breach for healthcare organizations is estimated to be more than $2.1 million; and
- The average cost of a data breach to Business Associates’ (BA) is more than $1 million.
Enforcing HIPAA Privacy and Security Rules by OCR is serious business. On March 16, 2016, the Feinstein Institute for Medical Research in New York entered into an agreement with the OCR to pay $3.9 million to settle violations of HIPAA rules. In addition to the penalty, Feinstein agreed to initiate a corrective plan to remediate deficiencies that led to the breach. This action stemmed from a September of 2012 incident when a laptop was stolen containing unencrypted, electronic PHI from a Feinstein employee’s car. The laptop contained information on approximately 13,000 Feinstein patients and research participants, including names, dates of birth, addresses, social security numbers, diagnoses, laboratory results, medications and other medical information regarding subjects’ participation in a research study. This case demonstrates OCRs commitment to enforcing and penalizing those who violate the HIPAA Privacy and Security Rules.
Despite the potential risk of financial exposure, half of all healthcare organizations surveyed in the PIABS report have little or no confidence in their ability to detect all patient data loss or theft. This is concerning because, for the first time in history, criminal attacks are the number one cause of data breaches in healthcare. Hacking healthcare’s technology infrastructure is up 125 percent compared to five years ago. The illustration below highlights the rise in hacking incidents.
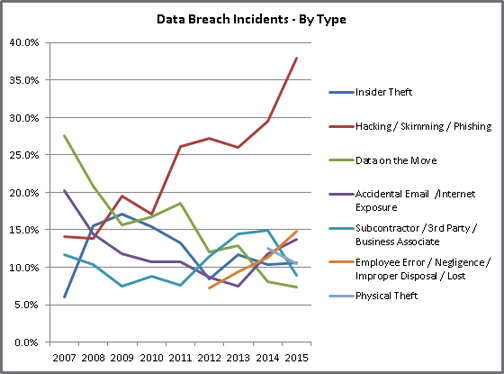
Source: Identity Theft Resource Center Breach Report Hits Near-Record High in 2015, http://www.idtheftcenter.org/ITRC-Surveys-Studies/2015databreaches.html
A new type of cyber-crime has emerged in the health industry affecting healthcare providers who have their data hijacked and held for ransom. Methodist Hospital, located in Henderson, Kentucky, has become the third healthcare entity in recent weeks to be victimized by ransomware. The first was Hollywood Presbyterian Medical Center in Los Angeles California, which paid $17,000 to the hackers to regain access to its electronic medical system, and the second known victim was Ottawa Hospital in Ontario, Canada, which had to wipe the system of the affected computers to regain access to its medical data. It appears that data held for ransom will continue to increase and will pose a serious business threat for covered entities and BAs.
Based on the rise in security threats, it would make sense that healthcare executives would be acutely focused on data security and make it a top priority, but they haven’t. According to the American College of Healthcare Executives’ (ACHE) annual survey of top issues confronting hospitals in 2015, Chief Executive Officer’s (CEO) ranked the top ten overarching issues affecting their hospitals, and they identified other specific areas of concern. There was more than 350 community hospital CEOs who participated in the survey.
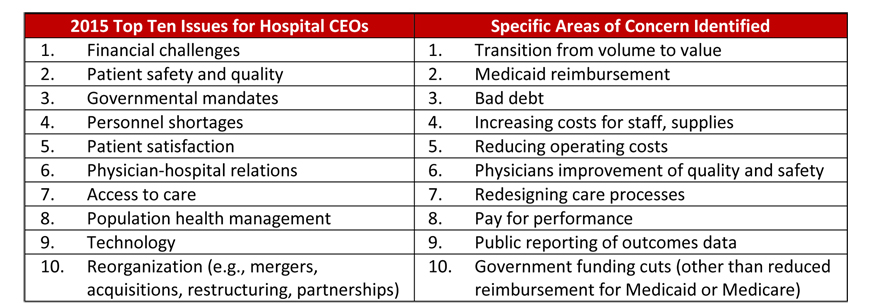
Implementation of Phase One and Two HIPAA Audits
Phase One of OCR’s PSBNR Audit Program has concluded. The program established critical national standards for the privacy and security of PHI and the Health Information Technology for Economic and Clinical Health Act (HITECH) and set breach notification requirements to provide greater transparency for individuals whose information may be at risk.
HITECH requires the OCR office to conduct audits of covered entities and BAs assuring adherence of the HPSBNR. In 2011 and 2012, OCR implemented the Phase One audit program to assess the controls and processes and conducted an extensive evaluation of the effectiveness of the pilot program. For more information about Phase One audits, you can view the post: OCR Releases Guidance Regarding Patients’ Access to PHI on MiraMed’s website.
Drawing on that experience and the results of the evaluation, OCR has implemented Phase Two of the program. According to OCR, Phase Two audits are designed to assess compliance with the HPSBNR for covered entities and their business associates. These audits will supplement OCR’s other enforcement tools, such as complaint investigations and reviews. OCR is attempting to identify best practices and proactively uncover and address risks and vulnerabilities to protected PHI.
Speaking at the 24th National HIPAA Summit in the District of Columbia on March 21, 2016, OCR Director Jocelyn Samuels announced the Phase Two launch, saying that the effort will comprise more than 200 desk and on-site audits. Samuels noted that OCR has also developed an audit-specific portal to enable notified entities to submit requested documentation in digital form.
Desk audits will make up the first two rounds of audits, Samuels said. The first series of desk audits will focus on covered entities, according to an OCR announcement, while the second round of audits will focus on business associates. By December 2016, all desk audits be completed. “We’ll be looking at risk analysis and risk management, notices of privacy practices and access and response to requests for access, and content timeliness of notifications,” Samuels said. Onsite audits, according to OCR, will focus on “a broader scope of requirements” compared to the desk audits.
The audit program, Samuels continued, will give OCR a way to examine different sectors and geographic regions of the industry, as well as different sized entities, to evaluate some of the risks they may be facing before those risks “ripen” into breaches.
“We don’t necessarily get to see these things through the complaints we receive, and by the time we get a breach report, it’s too late to prevent a problem,” she said. “We really do look at this as a valuable way for us to get out in front of potential problems and to direct our guidance to the issues that we see occurring in ways that we hope will be more useful to the regulated community.”
OCR’s Phase Two audits will increase industry cognizance of compliance requirements and identify where technical assistance is needed due to issues uncovered through the audits. The goal of the audit program is to give stakeholders the tools and guidance to improve industry compliance, self-evaluation and the prevention of breaches.
Concurrent with the recent Phase Two audit announcement, OCR has provided a list of 12 frequently asked questions on the HHS website to help covered entities and BAs better understand the program. They are:
1. When Will the Next Round of Audits Commence?
Phase Two of OCR’s HIPAA audit program is currently underway. OCR has begun to obtain and verify contact information to identify covered entities and business associates of various types and determine which are appropriate to be included in potential auditee pools. Communications from OCR will be sent via email and may be incorrectly classified as spam. If your entity’s spam filtering and virus protection are automatically enabled, we expect you to check your junk or spam email folder for emails from OCR; OSOCRAudit@hhs.gov.
2. Who Will Be Audited?
Every covered entity and business associate is eligible for an audit. These include covered individual and organizational providers of health services; health plans of all sizes and functions; healthcare clearinghouses; and a range of business associates of these entities. We expect covered entities and business associates to provide the auditors their full cooperation and support.
3. On What Basis Will Auditees Be Selected?
For this phase of the audit program, OCR is identifying pools of covered entities and business associates that represent a wide range of health care providers, health plans, health care clearinghouses and business associates. By looking at a broad spectrum of audit candidates, OCR can better assess HIPAA compliance across the industry–factoring in size, types and operations of potential auditees. Sampling criteria for auditee selection will include size of the entity, affiliation with other healthcare organizations, the type of entity and its relationship to individuals, whether an organization is public or private, geographic factors, and present enforcement activity with OCR. OCR will not audit entities with an open complaint investigation or that are currently undergoing a compliance review.
4. How Will the Selection Process Work?
Once entity contact information is obtained, a questionnaire designed to gather data about the size, type, and operations of potential auditees will be sent to covered entities and business associates. As a part of the pre-audit screening questionnaire, OCR is asking that entities identify their business associates. We encourage covered entities to prepare a list of each business associate with contact information so that they are able to respond to this request. OCR will conduct a random sample of entities in the audit pool. Selected auditees will then be notified of their participation.
If a covered entity or business associate fails to respond to information requests, OCR will use publically available information about the entity to create its audit pool. An entity that does not respond to OCR may still be selected for an audit or subject to a compliance review.
5. How Will the Audit Program Work?
OCR plans to conduct desk and onsite audits for both covered entities and their business associates. The first set of audits will be desk audits of covered entities followed by a second round of desk audits of business associates. These audits will examine compliance with specific requirements of the Privacy, Security, or Breach Notification Rules and auditees will be notified of the subject(s) of their audit in a document request letter. All desk audits in this phase will be completed by the end of December 2016.
The third set of audits will be onsite and will examine a broader scope of requirements from the HIPAA Rules than desk audits. Some desk auditees may be subject to a subsequent onsite audit.
The audit process will employ common audit techniques. Entities selected for an audit will be sent an email notification of their selection and will be asked to provide documents and other data in response to a document request letter. Audited entities will submit documents online via a new secure audit portal on OCR’s website. There will be fewer in-person visits during these Phase Two audits than in Phase One, but auditees should be prepared for a site visit when OCR deems it appropriate. Auditors will review documentation and then develop and share draft findings with the entity. Auditees will have the opportunity to respond to these draft findings; their written responses will be included in the final audit report. Audit reports generally describe how the audit was conducted, discuss any findings and contain entity responses to the draft findings.
6. What If an Entity Doesn’t Respond to OCR’s Requests for Information?
If an entity does not respond to requests for information from OCR, including address verification, the pre-screening audit questionnaire and the document request of those selected entities, OCR will use publically available information about the entity to create its audit pool. An entity that does not respond to OCR may still be selected for an audit or subject to a compliance review.
7. What is the General Timeline for an Audit?
In the coming months, OCR will notify the selected covered entities in writing through email about their selection for a desk audit. The OCR notification letter will introduce the audit team, explain the audit process and discuss OCR’s expectations in more detail. In addition, the letter will include initial requests for documentation. OCR expects covered entities that are the subject of an audit to submit requested information via OCR’s secure portal within 10 business days of the date on the information request. All documents are to be in digital form and submitted electronically via the secure online portal.
After these documents are received, the auditor will review the information submitted and provide the auditee with draft findings. Auditees will have 10 business days to review and return written comments, if any, to the auditor. The auditor will complete a final audit report for each entity within 30 business days after the auditee’s response. OCR will share a copy of the final report with the audited entity.
While conducting desk audits of covered entities, OCR will replicate the notification and document request process for initiating desk audits of selected business associates. OCR will share a copy of the final report with the audited business associate.
Similarly, entities will be notified via email of their selection for an onsite audit. The auditors will schedule an entrance conference and provide more information about the onsite audit process and expectations for the audit. Each onsite audit will be conducted over three to five days onsite, depending on the size of the entity. Onsite audits will be more comprehensive than desk audits and cover a wider range of requirements from the HIPAA Rules. Like the desk audit, entities will have 10 business days to review the draft findings and provide written comments to the auditor. The auditor will complete a final audit report for each entity within 30 business days after the auditee’s response. OCR will share a copy of the final report with the audited entity.
8. What Happens After an Audit?
Audits are primarily a compliance improvement activity. OCR will review and analyze information from the final reports. The aggregated results of the audits will enable OCR to better understand compliance efforts with particular aspects of the HIPAA Rules. Generally, OCR will use the audit reports to determine what types of technical assistance should be developed and what types of corrective action would be most helpful. Through the information gleaned from the audits, OCR will develop tools and guidance to assist the industry in compliance self-evaluation and in preventing breaches.
Should an audit report indicate a serious compliance issue, OCR may initiate a compliance review to further investigate. OCR will not post a listing of audited entities or the findings of an individual audit which clearly identifies the audited entity. However, under the Freedom of Information Act (FOIA), OCR may be required to release audit notification letters and other information about these audits upon request by the public. In the event OCR receives such a request, it will abide by the FOIA regulations.
9. How Will Consumers Be Affected?
The audit program is an important tool to help assure compliance with HIPAA protections, for the benefit of individuals. For example, the audit program may uncover promising practices, or reasons health information breaches are occurring and will help OCR create tools for covered entities and business associates to better protect individually identifiable health information. Concerns about compliance identified and corrected through an audit will serve to improve the privacy and security of health records. The technical assistance and promising practices that OCR generates will also assist covered entities and business associates in improving their efforts to keep health records safe and secure. During the audit process, OCR will continue to accept complaints from individuals and to launch compliance reviews where warranted; covered entities and business associates’ compliance obligations remain in full effect.
10. Will Audits Differ Depending on the Size and Type of Participants?
The audit protocols are designed to work with a broad range of covered entities and business associates, but their application may vary depending on the size and complexity of the entity being audited.
11. Will Auditors Look at State-Specific Privacy and Security Rules in Addition to HIPAA’s Privacy, Security and Breach Notification Rules?
No, the scope of the audit program does not extend beyond the Privacy, Security and Breach Notification Rules.
12. Who is Responsible for Paying the On-Site Auditors?
The Department of Health and Human Services is responsible for the onsite auditors. Neither covered entities nor their business associates are responsible for the costs of the audit program.
Summary
The Phase Two audit program is a work-in-progress. OCR has indicated that it will post updated audit protocols to reflect the HIPAA Omnibus Rulemaking and can be used as a tool for organizations to conduct their internal self-audits as part of their HIPAA compliance activities. OCR plans to develop new tools and guidance to assist the industry in compliance, self-evaluation and breach prevention strategies. The OCRs goal is to evaluate the results and procedures used in the Phase Two audits to develop a permanent audit program.
In preparation of the Phase Two audits, OCR recommends that covered entities and BAs pay extra attention to areas that represent “heightened risk.” They are:
- Risk assessment;
- Individuals’ right to access their PHI;
- Authorizations;
- Minimum necessary use and disclosure;
- Notice of privacy practices;
- Breach notification and incident response;
- Access controls;
- Encryption; and
- Logging.
Moreover, if covered entities and BAs focus on the following four primary HIPAA compliance actions, the likelihood of a positive outcome to a Phase Two audit is much greater. They are:
- Ensure the confidentiality, integrity and availability of all electronic protected health information the covered entity or business associate creates, receives, maintains, or transmits;
- Protect against any reasonably anticipated threats or hazards to the security or integrity of such information;
- Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required under [the regulations]; and
- Ensure compliance with [the regulations] by its workforce. 45 CFR §164.306(a).
Reference
1. 45 CFR § 164.502(e), 164.504(e), 164.532(d) and (e), A Business Associate is any company or person that is exposed to, handles or works with the data in medical records of the medical entities they are contracted with. http://www.hhs.gov/hipaa/for-professionals/privacy/guidance/business-associates/
______________________
Phil C. Solomon is the publisher of Revenue Cycle News, a healthcare business information blog and serves as the Vice President of Global Services for MiraMed, a healthcare revenue cycle outsourcing company. Phil has over 25 years’ experience consulting on a broad range of healthcare initiatives for clinical, financial and revenue cycle performance improvement and has worked with some of the industry’s largest health systems developing executable strategies for revenue enhancement, expense reduction, and clinical transformation. Previously, he was the CEO of a Fast Tech 50, healthcare technology firm, a principal executive at an INC Magazine’s top 500 Fastest Growing Private Companies in the U.S. and he has held various senior leadership positions with national and global business process outsourcing firms. He is an active member of the HFMA Georgia Chapter, has written over 250 articles about revenue cycle optimization and healthcare reform and is often featured as a speaker at industry educational events. You can reach him at philcsolomon@gmail.com, 404-849-8065 or on Twitter @philcsolomon.
The post 2016 Phase Two HIPAA Audit Program Update appeared first on REVENUE CYCLE NEWS.





